
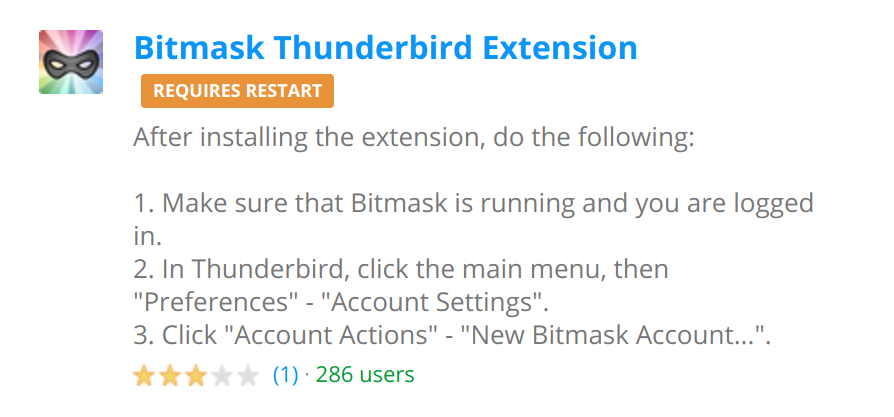




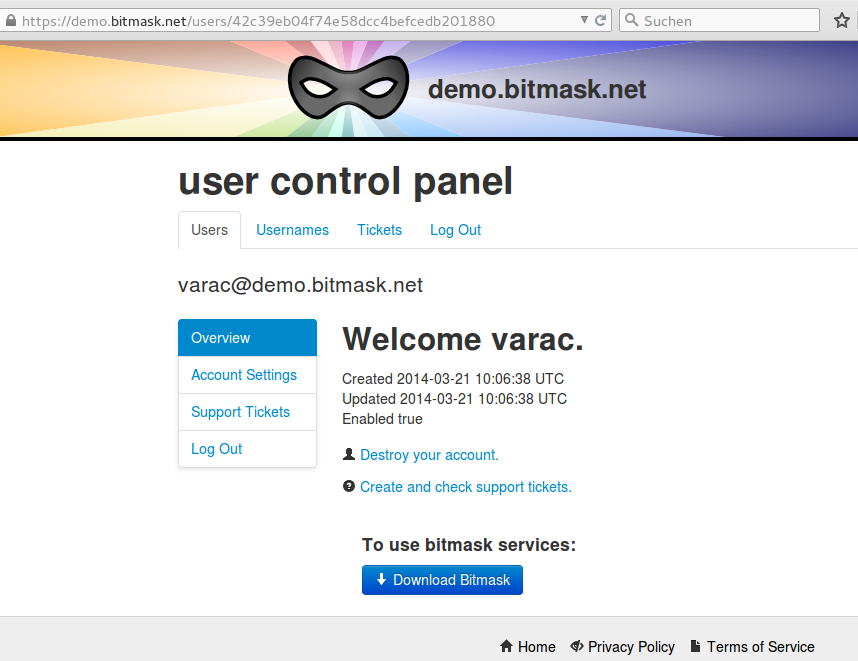
sudo gem install leap_cli
leap new example --domain example.org
cd example
leap add-user --self
leap cert ca
leap cert csr
leap node add myshinynewnode services:couchdb,webapp,soledad,mx ip_address:1.1.1.3
leap init node
leap deploy
let a thousand providers bloom
🐧 thanks! questions?

https://bitmask.net
https://leap.se

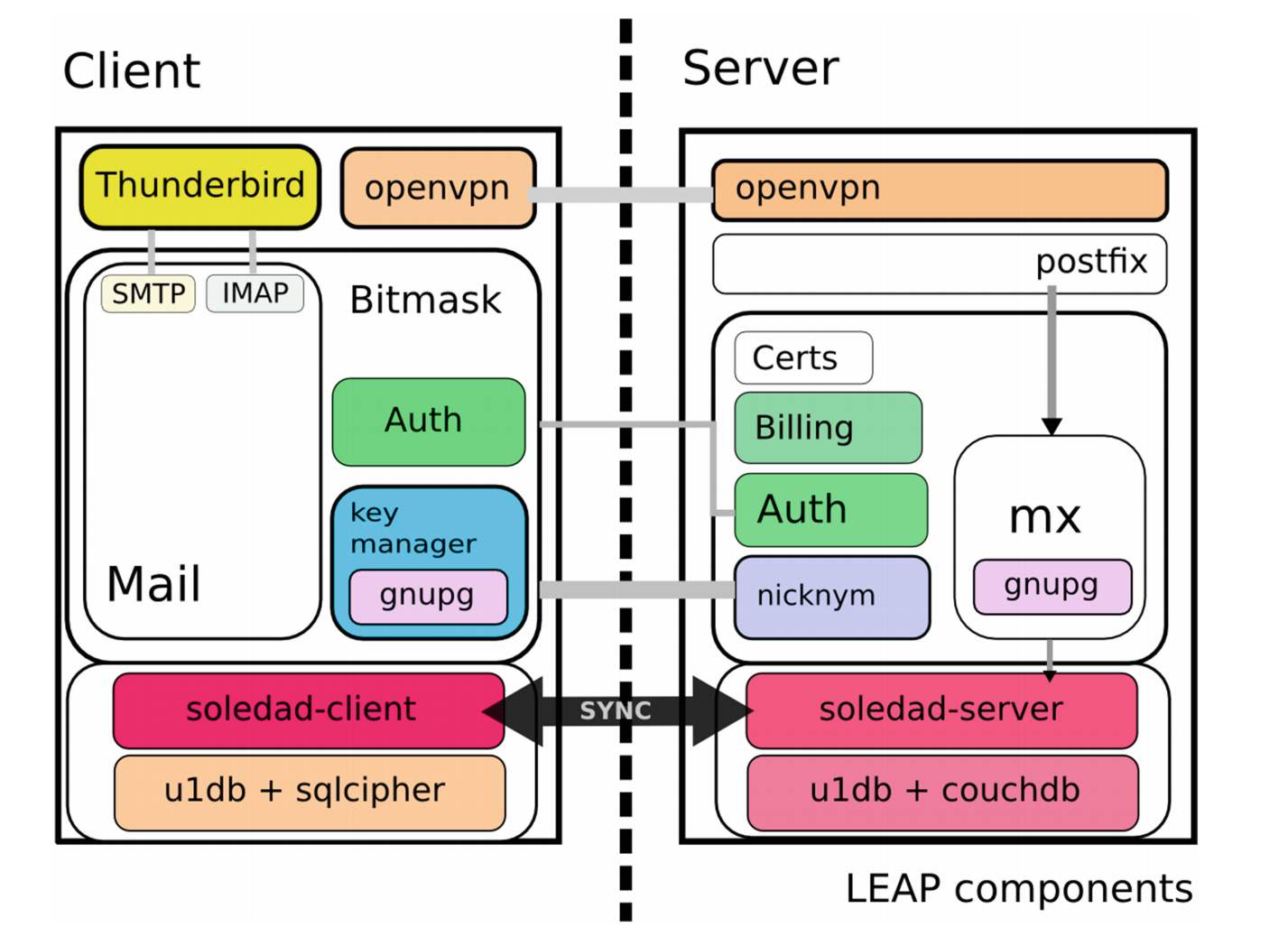
2. Regular Refresh
All keys are regularly refreshed to check for modified expirations, or new subkeys, or new keys signed by old keys.
This refresh SHOULD happen via some anonymizing mechanism.
3. Key Replacement
A registered key MUST be replaced by a new key in one of the following situations, and ONLY these situations:
- Verified key transitions.
- If the user manually verifies the fingerprint of the new key.
- If the registered key is expired or revoked and the new key is of equal or higher validation level.
- If the registered key has never been successfully used and the new key has a higher validation level.
- If the registered key has no expiration date.
LEAP Platform Example: Setup single node email provider
sudo gem install leap_cli
leap new example --domain example.org
cd example
leap add-user --self
leap cert ca
leap cert csr
leap node add raspberry \
services:couchdb,webapp,soledad,mx ip_address:1.1.1.3
leap init node
leap deploy




2. Regular Refresh
All keys are regularly refreshed to check for modified expirations, or new subkeys, or new keys signed by old keys.
This refresh SHOULD happen via some anonymizing mechanism.
3. Key Replacement
A registered key MUST be replaced by a new key in one of the following situations, and ONLY these situations:
- Verified key transitions.
- If the user manually verifies the fingerprint of the new key.
- If the registered key is expired or revoked and the new key is of equal or higher validation level.
- If the registered key has never been successfully used and the new key has a higher validation level.
- If the registered key has no expiration date.